Appliance settings
Use these procedures to configure appliance settings.
NOTE To configure a Recovery Series, Recovery MAX, or ION+ physical appliance for SAN-direct VMware backups, see VMware SAN-direct backups. (SAN-direct backups are not supported on Unitrends Backup or ION appliances.)
There are several addresses you should permit for all deployments. All of these ports are outgoing connections from the Unitrends appliance. We do not require incoming NAT of ports or exposing the unit to a public IP, only outgoing communication from a local source Unitrends appliance is needed.
IMPORTANT Never expose the appliance Web UI or SSH connections to open external ports. Doing so may void your support agreement until the appliance can be secured properly. Never deploy the Unitrends appliance on a public IP. All incoming ports to a Unitrends appliance must be firewall protected. Privately operated hot backup copy targets should be deployed in such a way as to secure the VPN connection to only trusted source external IPs.
During deployment, these network settings were configured for the appliance: IP address, subnet, gateway, primary DNS, hosts file, and open ports. Settings were either configured manually (if using a static IP address) or by DHCP.
● The IP address and subnet enable communication between the appliance and other machines on your network.
● The gateway enables communication between the appliance and machines on different subnets.
● Appliance DNS settings are required for the following:
● To connect the appliance to the Internet.
● To add assets using only their hostnames (rather than by fully qualified domain names).
● To add backup copy cloud targets to the appliance.
● To update your appliance from the UI.
● To access the Unitrends Community forums from the UI.
● The hosts file enables communication between the appliance and its protected assets without using DNS. (But DNS is required for other features and must be set up on the appliance.) During deployment, the hosts file is created and contains an entry for the appliance itself. Additional entries are automatically added to this file any time you add an asset to the appliance or configure a secure tunnel connection (for backup copy to the Unitrends Cloud or to another Unitrends appliance). In most cases it is not necessary to modify this file.
● Port security controls which ports are open on the appliance. By default, the appliance is configured with all ports open (port security is set to None Open All). Other port security levels are available and you can close ports by applying one of these other levels.
You can modify the network settings described above as needed. See the following for details:
NOTES
● Before changing network settings, you should verify that no jobs are running. Changing network settings while a job is running causes the job to fail.
● Do not edit the network settings of an adapter that is configured to use DHCP unless you intend to assign it a static IP address.
● If the appliance is being used as a backup copy target, you must assign a static IP address. DHCP is not supported for appliance backup copy targets.
● If you change the IP address, you will no longer be able to access the appliance from a web browser using the previous IP address. To avoid losing web access to your appliance, make sure to assign it valid network settings and to make a note of these new settings.
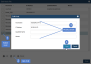
1. On the Configure > Appliances page, select the appliance.
2. Click the Network tab below.
3. Select the adapter and click Edit.
4. Enter the changes and click Save. See below for details.
● The options displayed in the Edit Network Adapter dialog differ by whether the appliance is running on CentOS 7 or CentOS 6. To check the Recovery OS Version, click on ? > About, as shown here:
For appliances running on CentOS 7, you can modify the following:
● To disable the adapter, select Off from the Configure Adapter Type list.
● If DHCP is available in your environment, you can switch from a static IP address to DHCP by selecting DHCP from the Configure Adapter Type list.
● To switch from DHCP to a static IP address, select Static from the Configure Adapter Type list and enter an IP Address, Gateway, Subnet, and DNS Settings.
1. On the Configure > Appliances page, select the appliance.
2. Click the Network tab below.
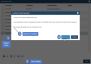
3. Select the adapter and click Edit Hosts File.
4. Do any of following:
● To add an asset, click Add, enter all applicable information, and click Save:
● To edit an asset, select it in the list, click Edit, modify information, and click Save:
● To delete an asset, select it in the list, click Delete, check the I understand the risks... box, and click Delete Host:
5. Review your changes and click Close to exit.
NOTE If this appliance is managed by UniView (e.g., users can only log in to the appliance UI from UniView), you cannot modify port security settings. The Ports tab is disable and you receive a Managed by UniView message if you attempt to click the tab.
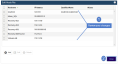
1. Log in to the appliance UI.
You must log in directly to the appliance. You cannot change the port security settings of a managed appliance.
2. On the Configure > Appliances page, select the appliance.
3. Click the Network tab below.
4. Select the adapter and click Ports.
5. View the Port Security area to see the current port security setting and to determine which setting you want to apply. Click each option to see the associated closed ports:
● None (Open All) opens all ports.
● Low, Medium, and High closes the ports listed in the table above.
6. Select a Port Security option and click Save.
Additional ports must be open for connectivity to the Internet and for connectivity to any hot backup copy target. See the following for details:
NOTE Unitrends does not officially support backup through firewalls. For details, see this KB article: Backup fails through Router, DMZ, or Firewall.
|
Task |
Port, Protocol, and Rule |
Destination |
Notes |
|---|---|---|---|
|
Backup and backup copy operations |
443/HTTPS Outbound from the Unitrends appliance |
kaseyagroup-appliance-registry.jfrog.io |
A secure docker container registry required to update backup and backup copy components. |
|
Product Updates |
443/HTTPS Outbound from the Unitrends appliance
22/SFTP Outbound from the Unitrends appliance |
repo.unitrends.com
sftp.unitrends.com
|
repo.unitrends.com is used by the Unitrends appliance to perform software updates.
sftp.unitrends.com is used to collect files related to active support tickets. |
|
Remote Support |
443/HTTPS Outbound from the Unitrends appliance |
support-itivity.unitrends.com |
Used for opening a remote tunnel to the Unitrends support team. |
|
Proactive Monitoring |
161/UDP Outbound from the Unitrends appliance 161/TCP Outbound from the Unitrends appliance 162/UDP Outbound from the Unitrends appliance 162/TCP Outbound from the Unitrends appliance |
notifications.unitrends.com |
Used for SNMP trap collection for all proactive monitoring. |
|
Task |
Port, Protocol, and Rule |
Destination |
Notes |
|---|---|---|---|
|
Backup copy to the Unitrends Cloud or your Unitrends target appliance. |
The OpenVPN port provided by Unitrends Or The port number you have configured for the secure tunnel connection to the backup copy target appliance must be open Outbound for the TCP and UDP protocols. Port 443 must also be open Outbond for the UCP protocol. |
For Unitrends Cloud, the public-facing IP address provided by Unitrends.
Target appliance hostname and IP |
Used for copying data to the Unitrends Cloud or your Unitrends target appliance. |
1. On the Configure > Appliances page, select the appliance and click Edit.
2. Select the Email tab.
3. Check the Enable email reporting option.
4. Enter the fully qualified SMTP server name or its IP address.
NOTE If a DNS record has not been configured, you must use the IP address of the SMTP server.
5. If you have an externally-hosted SMTP server that requires authentication, check the Server requires credentials option and enter username and password credentials.
IMPORTANT
● When using a non-local mail server or an internal SMTP relay configuration, we recommend using an authenticated mail user to prevent filtering issues (for example, cases where alerts are not sent to specific recipients due to filtering rules applied to unauthenticated connections or defined in the mail domain policy). Use a mail user service account that is exempt from routine password change to prevent email from being blocked or delayed.
● Google security requirements – As of May 30, 2022, Google no longer supports the use of third-party apps or devices which ask you to sign in to your Google Account using only your username and password (for details, see Less secure apps & your Google Account). To use Gmail as an SMTP relay, you must:
● Create an application password for the Unitrends appliance in the Google Account:
● Access the Google account and go to Manage Google Account > Security > App passwords.
● From the Select app list, select Other (Custom name). Enter a custom name (e.g., Unitrends).
● Click Generate. The Google app password is generated and displays on the Generated app password page.
● On the Email tab of the Unitrends Edit Appliance dialog, check Server requires credentials and enter the Google username and the 16-digit, Google-generated app password.
6. To test the SMTP configuration, click Send a Test Email. Enter your email address and click Send. The appliance sends a test email. (If you do not receive the email, check the SMTP settings.)
7. Enter an email recipient and select the email report types that this recipient will receive.
(Optional) Click + to add more recipients. For further information on email report types, see Email reports .
● Appliance — Appliance Status, Replication Activity (if hot backup copy is configured), and Compliance (if data copy access jobs are scheduled) reports are sent to the recipient if this option is selected.
● Jobs — The Schedule report is sent to the recipient if this option is selected.
● Failures — Failure reports are sent to the recipient if this option is selected.
8. Click Save.
Unitrends appliances are managed and monitored from the User Interface (UI). A user account is required to access the UI. By default, a superuser named root is created on the appliance, but you can create additional user accounts. You can set up users on the appliance itself or use Active Directory (AD) authentication.
A user's role determines what the user can access on the appliance. Roles are assigned to users in these ways:
● When you create a user on the appliance, you assign a role to the user.
● If you are using AD authentication, you add Unitrends AD user groups to your AD domain (as AD security groups) and assign users to these groups. Each Unitrends AD user group comes configured with a Unitrends role that is applied to each user in the group.
See these topics for details on how role-based access works:
Unitrends' self service role-based access control model enables you to restrict a user's access at the appliance, asset, and task level. Each user account is assigned a role that defines the types of operations the user can perform on the appliance. In addition, the Manage role can be further customized by applying an access level and other options. User roles and access levels are described in the following table.
|
Role |
Access level |
Description |
|---|---|---|
|
Monitor |
not applicable |
A user with this role is only able to view the status of operations, such as jobs, and to run reports. The user cannot create or start jobs or configure the appliance in any way. |
|
Manage |
No Restrictions |
A user with this role and access level can: ● View all settings and run reports. ● Perform all backup, backup copy, and recovery tasks (create, modify, run, cancel, and delete jobs, delete backups, recover backups, etc.). ● Perform all other management and configuration tasks other than creating or modifying users. (The user can add, modify, and delete assets, managed appliances and backup copy targets, modify network, storage, and email settings, edit their password, etc.). NOTE If using Active Directory authentication, users in the Unitrends-Manage AD group have the No Restrictions access level. You cannot modify the access level of a Unitrends AD group. However, you can add a Unitrends-Manage AD user to the UI and apply a different access level. For details, see To add a role to a user in the Unitrends-Manage AD group. |
|
Manage |
Backup/Recovery Operator |
A user with this role and access level can: ● Run reports. ● View jobs. ● Run, cancel, suspend, or resume existing backup and backup copy jobs. (The user cannot create, modify, or delete backup or backup copy jobs.) ● Recover from backups and backup copies. ● Cancel active recovery jobs. You can further restrict recovery operations by using: ● Edit Scope to specify the assets the user can access. ● The user can recover from backups and backup copies of in-scope assets only. Backups and backup copies of other assets do not display in the UI and cannot be accessed by the user. ● The user can cancel active recovery jobs of in-scope assets only. Recovery jobs of other assets display in the UI but the user cannot cancel these jobs. NOTE VMware vApps and resource pools cannot be excluded from a user's scope. If the user has access to any hosted VM on an ESXi server, the user can access its hosted vApps and resource pools. ● Edit Options to restrict what and how the user can recover from backups and backup copies. (For example, recover only files, recover only to the original asset, etc.). |
|
Manage |
Backup Operator |
A user with this role and access level can: ● Run reports. ● View jobs. ● Run, cancel, suspend, or resume existing backup and backup copy jobs. (The user cannot create, modify, or delete backup or backup copy jobs.) |
|
Manage |
Recovery Operator |
A user with this role and access level can: ● Run reports. ● View jobs. ● Recover from backups and backup copies. ● Cancel active recovery jobs. You can further restrict recovery operations by using: ● Edit Scope to specify the assets the user can access. ● The user can recover from backups and backup copies of in-scope assets only. Backups and backup copies of other assets do not display in the UI and cannot be accessed by the user. ● The user can cancel active recovery jobs of in-scope assets only. Recovery jobs of other assets display in the UI but the user cannot cancel these jobs. NOTE VMware vApps and resource pools cannot be excluded from a user's scope. If the user has access to any hosted VM on an ESXi server, the user can access its hosted vApps and resource pools. ● Edit Options to restrict what and how the user can recover from backups and backup copies. (For example, recover only files, recover only to the original asset, etc.). |
|
Superuser or Administrator |
not applicable |
A user with this role can perform all operations, including adding, editing, and deleting users. |
Review these additional considerations before managing users:
● User accounts can only be used to log in to the appliance for which they were created. Users are not shared across Unitrends appliances. To log in to another appliance, the user must be created directly on that appliance.
● Once a user logs in, they can access the local appliance and any appliances that are managed by the local appliance. The user's role determines the operations they can perform on the local and managed appliances.
● To add, modify, or delete users, you must be logged in to the UI as a user that has the administrator or superuser role. Users with monitor or manage roles can only see their own user account.
● To add a user, you must supply a username, password, and role for the new user.
● Once you set up users, you can assign them to asset groups to customize how protected assets are grouped and displayed for the user in the UI. For details, see Grouping assets in custom folders.
● In most cases, you access the appliance through the UI by entering UI user and password credentials. If you are an advanced user and need command line access, you can use a terminal emulator, such as PuTTY, to connect to the appliance using operating system account credentials. The appliance's OS root user is the only account that can be used for command line access. Use caution when performing tasks from the appliance command line. Before using the command line, check the Support Toolbox. Many lower-level appliance tasks can be run from this handy interface.
See these procedures to manage appliance UI users:
1. Log in to the appliance as a user that has the administrator or superuser role.
2. On the Configure > Appliances page, select the appliance and click Edit.
3. Select the Users tab.
4. Click Add.
5. In the Add User area, enter the Username, Password, and Confirm Password, then select a Role. For a description of each role, see Roles and access levels.
6. Do one of the following:
● If you selected the Manage role, continue with step 7.
● If you did NOT select the Manage role, skip to step 11.
7. Select an Access Level. For a description of each access level, see Roles and access levels.
8. Do one of the following:
● If you selected the Recovery Operator or Backup/Recovery Operator access level, continue with step 9.
● If you selected the No Restrictions or Backup Operator access level, skip to step 11.
9. (Optional) Restrict the assets the user can access for recovery tasks. Skip this step if you want the user to have access to all assets. (For details on how restricting assets works, see Roles and access levels.)
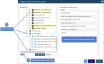
Restrict access to assets by doing these steps:
● Click Edit Scope.
● In the Inventory area, check boxes to select each asset the user will have access to. Selected assets display in the Recovery Scope Assets area.
● You can expand nodes in the inventory tree to view and select hosted applications and VMs.
● You can select a virtual host or application instance to enable access to all of its hosted VMs or databases. Note that as new VMs and databases are added they are not automatically added to the user's scope. To add them, edit the AD user role to discover the new VMs or databases.
NOTE VMware vApps and resource pools cannot be excluded from a user's scope. If the user has access to any hosted VM on an ESXi server, the user can access its hosted vApps and resource pools (even if you do NOT select them in the inventory tree to add them to the Recovery Scope Assets list).
● Click Save.
10. (Optional) Restrict the user's recovery options. Skip this step if you want the user to have the ability to perform all recovery operations.
Restrict recovery options by doing these steps:
● Click Edit Options.
● In the Recovery Options dialog, select one or more options, then click Save.
|
Recovery option |
Description |
|---|---|
|
Only allow file recovery, not recovery of an entire backup |
Check this box to allow the user to recover only selected files from a backup or backup copy. The user is not able to recover any of the following: ● An entire backup. ● An entire virtual machine from a host-level backup. ● A virtual machine by using instant recovery. ● A Windows asset by using Windows replicas. ● An asset by using bare metal recovery. |
|
Only allow recovery to the original asset |
Check this box to allow recovery to the original asset only. The user is not able to recover to a different asset. |
|
Do not allow in-place SQL database restores |
Check this box to prevent SQL database restores to the original location. The user can only recover SQL backups to an alternate location. The user is not able to recover any of the following; ● System databases (master, model, and msdb). ● Stretch databases. |
|
Do not allow downloads from a Hot Backup Copy target |
Check this box to prevent the user from recovering from backup copies that reside in the Unitrends Cloud or on a remote hot backup copy target. The user can recover from local hot backup copies only (hot copies that reside on the appliance they are logged in to). The user is not able to: ● Import a hot backup copy from a remote target to the local appliance. ● Download files from a hot backup copy that resides on a remote target. |
|
Exclude these suffixes during agent-based file level recovery |
Applies to recovering files from file-level backups only. This restriction does not apply to recovering entire file-level backups or recovering from other backup types (such as host-level or application backups). Enter a comma-separated list of file extensions to prevent the user from recovering files of these types. You must include the * wildcard before each extension. For example, enter the following to exclude ZIP files, HTML files, and executables: *.zip, *.html, *.exe |
11. Click Add to add the new user.
12. Click Save.
1. Log in to the appliance as a user that has the administrator or superuser role.
2. On the Configure > Appliances page, select the appliance and click Edit.
3. Select the Users tab.
4. Select a user in list, then click Edit.
5. Modify fields, then click Update. (For details on each setting, see To add a user.)
6. Click Save.
See these procedures to manage Active Directory users:
You can use Active Directory (AD) domain credentials for Unitrends user accounts. Set Unitrends users up as members of specified AD domains and they can access the appliance without being added as users on the appliance itself.
NOTE AD authentication is implemented at the UI and Apache component level. The Unitrends operating system is not joined to the AD domain.
The AD security group to which a user belongs determines which features that user can view and utilize. Users are granted one of the following roles: monitor, manage, administrator, or superuser.
Use these steps to set up AD authentication:
1. Create the following security groups in your Active Directory domain. For a description of each role, see Roles and access levels.
|
AD security group |
Description |
|---|---|
|
Unitrends-Superuser |
Members of this security group are granted the superuser role in the Unitrends UI. |
|
Unitrends-Admin |
Members of this security group or BULTIN\administrators are granted the administrator role in the Unitrends UI. |
|
Unitrends-Manage |
Members of this security group are granted the manage role and no restrictions access level in the Unitrends UI. These users can view statuses and reports, run jobs, and perform other management tasks, such as adding or modifying assets and retention settings. You can restrict a user's backup and recovery options by adding the AD user to the UI and applying a different access level. For details, see To add a role to a user in the Unitrends-Manage AD group. |
|
Unitrends-Monitor |
Members of this security group are granted the monitor role in the Unitrends UI. These users are only able to view the status of completed jobs and run reports. They cannot run jobs, view running jobs, or configure the appliance in any way. |
NOTE You may name these security groups to suit your environment. If you use your own names, be sure to enter those names when you configure AD authentication on the appliance. Unitrends AD user group names in your AD domain must match the names you enter below in step 8.
2. Add users to the Unitrends AD security groups as desired.
Users who are not BULTIN\administrators must be assigned to a Unitrends group to log in to the UI using AD authentication.
NOTE Add users to the groups only. Do not add groups. Nested grouping is not a Microsoft best practice and may cause undesirable results.
3. Do one of the following:
● Create a DNS entry for the AD server with reverse lookup configured, then skip to step 8.
● Continue with step 4. to add the AD server to the Unitrends appliance's hosts file.
4. Log in to the appliance UI as a user that has the administrator or superuser role.
5. On the Configure > Appliances page, select the appliance and click the Network tab below.
6. Click Edit Hosts File.
7. Add the Active Directory server to the appliance hosts file:
NOTE This host entry must be added before you configure the appliance for AD authentication.
● Click Add.
● Enter the Host Name of the AD server that manages the Active Directory domain.
● Enter the IP Address of the AD server.
● For Qualified Name, enter the Active Directory domain only. Do not include the server name.
● Click Save.
● Example: for an AD server called SERVER_AD whose IP address is 192.168.111.75 and AD domain is company_domain.com, enter the following:
● SERVER_AD in the Host Name field
● 192.168.111.75 in the IP Address field
● company_domain.com in the Qualified Name field
8. Configure the appliance for AD authentication. Click Modify AD Settings and enter the following in the Current Active Directory Settings area:
|
Field |
Action |
|---|---|
|
Enable Active Directory Authentication |
Check this box to start using AD authentication, or leave unchecked to start using AD authentication at a later time. |
|
Use SSL |
The Use SSL option is not used. |
|
Active Directory Server |
Enter the hostname of the AD server that manages the Active Directory Domain. If left blank, the appliance populates this field using the hosts file entry. If you are using DNS and did not add the AD server to the hosts file, be sure to enter the hostname here. This field is limited to 15 characters. |
|
Active Directory Domain |
Enter the name of the AD domain. Do not include the AD server name. For example, ad_domain.company_domain.com. This name must be present in the appliance hosts file or resolvable through DNS. |
|
Active Directory IP |
Displays the IP of the AD server if you added it to the appliance hosts file. (No IP displays if you are using DNS.) |
|
Unitrends user groups |
Unitrends AD user groups display below the Active Directory IP. If you opted to enter different user group names above in step 1. , modify the names here to match those that you entered. User group names in these fields must match the names in your AD domain. |
9. Click Save.
Users in the Unitrends AD groups can now log in to the appliance UI by using their AD credentials. Note that AD users do not display on the Users tab in the Unitrends UI (unless you add an AD user role for the user).
Users in the Unitrends-Manage group are granted the no restrictions access level. You can restrict a user's backup and recovery options by adding the AD user to the UI and applying a different access level. For details, see To add a role to a user in the Unitrends-Manage AD group.
This procedure assumes you have set up the Unitrends user account in Active Directory and have configured AD authentication as described in To set up Active Directory authentication.
1. Connect to the appliance by directing a Chrome or Firefox browser to:
https://<appliance IP address>ui/
2. On the Login page, enter the AD domain and user name in either of the following formats:
ad_domain\ad_username or ad_username@ad_domain.company_domain.
For example, for user jsmith on AD domain accounting and company domain americanaccountants.com, enter:
accounting\jsmith
or
jsmith@accounting.americanaccountants.com
3. Enter the password for this AD user.
4. Click Login.
Once you have set up AD authentication, users that have been added to the Unitrends AD security groups in your AD domain can log in to the appliance and perform operations that are enabled for their group. No further setup is required.
For users in the Unitrends-Manage security group, you have the option to apply additional restrictions by adding AD user roles. Once you add a user role, the AD user displays in the list of users on the Users tab. (AD users that do not have roles defined do not display in the Unitrends UI.)
NOTE Adding a user role is supported for AD users with the manage role only (users in the Unitrends-Manage group, if you are using the default Unitrends group names). Because the appliance cannot determine a user's role in your AD domain, the UI does not prevent assigning roles to AD users that have the monitor, administrator, or superuser roles. Be aware that the access level you assign by doing this procedure only applies if the user has the manage role in your AD domain. If not, the access level is not used and the user's role (monitor, administrator, or superuser) determines the operations they can perform.
Use this procedure to add an AD user role:
1. Log in to the appliance as a user that has the administrator or superuser role.
2. On the Configure > Appliances page, select the appliance and click Edit.
3. On the Edit Appliance dialog, select the Users tab.
4. Click Add AD User Role at the bottom of the tab.
5. Enter the AD Username. Do not include the AD domain or company domain. For example, for user jose.perez on AD domain accounting and company domain americanaccountants.com, enter: jose.perez
6. Select an Access Level. For a description of each access level, see Roles and access levels.
7. Do one of the following:
● If you selected the Recovery Operator or Backup/Recovery Operator access level, continue with step 8.
● If you selected the No Restrictions or Backup Operator access level, skip to step 10.
8. (Optional) Restrict the assets the user can access for recovery tasks. Skip this step if you want the user to have access to all assets. (For details on how restricting assets works, see Roles and access levels.)
Restrict access to assets by doing these steps:
● Click Edit Scope.
● In the Inventory area, check boxes to select each asset the user will have access to. Selected assets display in the Recovery Scope Assets area.
● You can expand nodes in the inventory tree to view and select hosted applications and VMs.
● You can select a virtual host or application instance to enable access to all of its hosted VMs or databases. Note that as new VMs and databases are added they are not automatically added to the user's scope. To add them, edit the AD user role to discover the new VMs or databases.
NOTE VMware vApps and resource pools cannot be excluded from a user's scope. If the user has access to any hosted VM on an ESXi server, the user can access its hosted vApps and resource pools (even if you do NOT select them in the inventory tree to add them to the Recovery Scope Assets list).
● Click Save.
9. (Optional) Restrict the user's recovery options. Skip this step if you want the user to have the ability to perform all recovery operations.
Restrict recovery options by doing these steps:
● Click Edit Options.
● In the Recovery Options dialog, select one or more options, then click Save.
|
Recovery option |
Description |
|---|---|
|
Only allow file recovery, not recovery of an entire backup |
Check this box to allow the user to recover only selected files from a backup or backup copy. The user is not able to recover any of the following: ● An entire backup. ● An entire virtual machine from a host-level backup. ● A virtual machine by using instant recovery. ● A Windows asset by using Windows replicas. ● An asset by using bare metal recovery. |
|
Only allow recovery to the original asset |
Check this box to allow recovery to the original asset only. The user is not able to recover to a different asset. |
|
Do not allow in-place SQL database restores |
Check this box to prevent SQL database restores to the original location. The user can only recover SQL backups to an alternate location. The user is not able to recover any of the following; ● System databases (master, model, and msdb). ● Stretch databases. |
|
Do not allow downloads from a Hot Backup Copy target |
Check this box to prevent the user from recovering from backup copies that reside in the Unitrends Cloud or on a remote hot backup copy target. The user can recover from local hot backup copies only (hot copies that reside on the appliance they are logged in to). The user is not able to: ● Import a hot backup copy from a remote target to the local appliance. ● Download files from a hot backup copy that resides on a remote target. |
|
Exclude these suffixes during agent-based file level recovery |
Applies to recovering files from file-level backups only. This restriction does not apply to recovering entire file-level backups or recovering from other backup types (such as host-level or application backups). Enter a comma-separated list of file extensions to prevent the user from recovering files of these types. You must include the * wildcard before each extension. For example, enter the following to exclude ZIP files, HTML files, and executables: *.zip, *.html, *.exe |
10. Click Add to add the role. The AD user role displays in the list of users above.
11. Click Save to exit the Edit Appliance dialog.
1. Log in to the appliance as a user that has the administrator or superuser role.
2. On the Configure > Appliances page, select the appliance and click Edit.
3. On the Edit Appliance dialog, select the Users tab. AD users that have roles defined display in the user list.
4. Select the AD user in the list, then click Edit.
5. Modify user role settings, then click Update. (For details on each setting, see To add a role to a user in the Unitrends-Manage AD group.)
6. Click Save to exit the Edit Appliance dialog.
1. Log in to the appliance as a user that has the administrator or superuser role.
2. On the Configure > Appliances page, select the appliance and click Edit.
3. On the Edit Appliance dialog, select the Users tab. AD users that have roles defined display in the user list.
4. Select the AD user.
5. Click Remove, then Confirm. The user role is removed.
6. Click Save to exit the Edit Appliance dialog.
Add the user to one of the Unitrends AD security groups in your Active Directory domain.
Remove the user from its Unitrends AD security group in your Active Directory domain.
Use this procedure to enable or disable AD authentication, modify AD server settings, and modify Unitrends AD security group names.
NOTE Unitrends AD security group names entered in the Active Directory Settings dialog must match the names defined in your AD domain. Only modify the Unitrends AD group names if these names have changed in your AD environment.
1. Log in to the appliance as a user that has the administrator or superuser role.
2. On the Configure > Appliances page, select the appliance and click Edit.
3. On the Edit Appliance dialog, select the Users tab.
4. Click Modify AD Settings at the bottom of the tab.
5. Modify information as needed and click Save. For details on each setting, see To set up Active Directory authentication.
Users log in to the appliance UI by supplying UI user and password credentials. These UI users are created as described in Users and roles. In addition to these UI users, the appliance also has an operating system account for command line access.
Use these procedures to manage passwords:
1. Log in to the UI as a user that has the superuser or administrator role.
2. On the Configure > Appliances page, select the appliance and click Edit.
3. Select the Users tab.
4. Select a user in list, then click Edit.
5. Click Change (to the right of Password).
6. Enter the Current Password, New Password and Confirm Password.
7. Click Update.
8. Click Save.
In most cases, you access the appliance through the UI by entering UI user and password credentials. If you are an advanced user and need command line access, you can use a terminal emulator, such as PuTTY, to connect to the appliance using operating system account credentials (user root). Use caution when performing tasks from the appliance command line. Before using the command line, check the Support Toolbox. Many lower-level appliance tasks can be run from this handy interface.
During deployment, date and time settings were configured for the appliance. You can edit these settings as needed. You can manually set the date and time or sync to an NTP server. To use an NTP server, you will need to supply its address. Edit these settings from the Date Time tab of the Configure > Appliances > Edit > Edit Appliance page.
To edit date and time settings
1. On the Configure > Appliances page, select the appliance and click Edit.
2. Select the Date Time tab.
3. Do one of the following:
● Select Enter a date and time for your appliance, specify a Date, Time, and Timezone, then click Save:
● Select Use an NTP Server to sync the appliance date and time to one of the NTP servers in the list. (Or you can opt to add your own NTP server by entering its NTP Server Address and clicking Add.) Click Save to sync to the NTP server:
You can add or modify the appliance license as needed.
NOTE Applying a license stops all running jobs.
Licensing procedures for physical Recovery Series, Recovery MAX, and ION/ION+ appliances differ from those for virtual Unitrends Backup appliances:
● Recovery Series, Recovery MAX, and ION/ION+ appliances ship fully licensed. It is likely you will never need to modify this license unless directed to do so by Unitrends Support. If you need to update a license, apply the license you receive from Unitrends.
● Unitrends Backup appliances deploy without a license. Register the license as described in To register a Unitrends Backup appliance, then apply the license you receive from Unitrends as described in To license a Unitrends Backup appliance.
1. On the Configure > Appliances page, select the appliance and click Edit.
2. Select the License tab and click Update. The Registration Center displays.
3. Select one of the following:
|
Selection |
Description |
|---|---|
|
Start my free trial |
Submit this form to start your free 30-day trial. |
|
Activate my purchase |
Enter your email address and activation code. You license key will be emailed to the address you enter here. |
|
Activate with promo code |
Enter your promotional code to register your product and receive your license key. |
|
Request a quote |
Request a license quote. |
4. Complete and submit the applicable form.
Once you have purchased a license, Unitrends sends an email containing license details. Use the next procedure to apply this license information to the appliance.
Use these steps to enter license information you have received from Unitrends.
1. On the Configure > Appliances page, select the appliance and click Edit.
2. Select the License tab and click Add License Info.
3. Enter the License Key, Expiration Date, and Feature String.
4. Click Save. The license is applied.
Use these steps to see the number of application, server, socket, VM, and workstation resources you can protect with your license, and the appliance's current resource usage.
1. On the Configure > Appliances page, select the appliance and click Edit.
2. Select the License tab and click Resources.
3. Resource limits and usage display.
4. Click Close to exit.
Use encryption to protect data from unauthorized access and theft. All data remains encrypted until a request is made to recover the data. If the correct passphrases are in place, recovery proceeds without administrator involvement.
Unitrends encryption provides:
● Encryption at the asset level.
● The ability to manage and change passphrases.
● Backup, backup copy, and recovery of encrypted data.
To set up encryption, you provide a passphrase and save the master key file. Once you configure encryption, you can encrypt backups by asset (Configure > Protected Assets > Edit Asset). See these topics for details:
The following encryption limitations apply:
● Encryption slightly degrades performance for backups, backup copies, and recovery. Use encryption only if you really need to hide your data.
● Make sure to keep the passphrase secure. If you forget the passphrase, there is no way to recover it or recover any encrypted backups.
● Once you have enabled encryption for an asset, that asset’s subsequent backups are encrypted. Encryption takes place during backup jobs. When unencrypted backups run on an appliance before you configure encryption, those backups remain unencrypted.
● Small Form Factors (SFF) do not support encryption.
● The following backup types are not encrypted:
● Legacy MS Exchange Information Store backups
● CEP brick-level backups
● Any data stored on the appliance via Samba or NFS
1. On the Configure > Appliances page, select the appliance and click Edit.
2. Select the Advanced tab.
3. Check Enable Encryption.
4. Enter a Passphrase and Confirm Passphrase.
IMPORTANT Be sure to keep the passphrase secure. If you forget the passphrase there is no way to recover it.
5. Click Save.
6. Return to the Edit Appliance dialog.
7. Select the Advanced tab and click Save Master Key File.
8. (Optional) If your appliance has a CD drive, you can save the key file directly to a CD. Insert a CD into your appliance's CD drive. (If no CD is inserted, the key file is saved to the appliance's samba share.)
9. Click Continue.
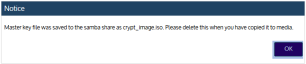
10. You receive a message indicating the master key file was saved to the appliance's samba share or to CD. Click OK.
IMPORTANT Be sure to keep the master key file secure. If you ever need to perform disaster recovery of the appliance, you will need this key to access any encrypted backups.
11. If you saved the key to the appliance's samba share, do these steps:
● Log in to a Windows workstation as an administrator with full system access.
● Launch File Explorer and enter the following path to access the master key file on the Unitrends appliance: \\ApplianceIP\samba
● Copy the master key file, called crypt_image.iso, to removable media and store it in a safe location.
● Once you have copied the key to removable media, delete crypt_image.iso from \\ApplianceIP\samba for increased security.
12. Enable encryption for each asset whose backups you wish to encrypt. To enable encryption for an asset, go to Configure > Protected Assets. Select the asset, click Edit, select Encrypt Backups, then Save.
1. On the Configure > Appliances page, select the appliance and click Edit.
2. Select the Advanced tab.
3. Enter the Current Passphrase.
4. Check Change Passphrase and enter a New Passphrase and Confirm New Passphrase.
IMPORTANT Be sure to keep the passphrase secure. If you forget the passphrase there is no way to recover it.
5. Click Save Master Key File.
6. (Optional) If your appliance has a CD drive, you can save the key file directly to a CD. Insert a CD into your appliance's CD drive. (If no CD is inserted, the key file is saved to the appliance's samba share.)
7. Click Continue.
8. You receive a message indicating the master key file was saved to the appliance's samba share or to CD. Click OK.
IMPORTANT Be sure to keep the master key file secure. If you ever need to perform disaster recovery of the appliance, you will need this key to access any encrypted backups.
9. Click Save in the Edit Appliance dialog.
10. If you saved the key to the appliance's samba share, do these steps:
● Log in to a Windows workstation as an administrator with full system access.
● Launch File Explorer and enter the following path to access the master key file on the Unitrends appliance: \\ApplianceIP\samba
● Copy the master key file, called crypt_image.iso, to removable media and store it in a safe location.
● Once you have copied the key to removable media, delete crypt_image.iso from \\ApplianceIP\samba for increased security.
NOTE After adding the appliance to UniView, it is recommended that you disable local network access for increased security. Once local network access is disabled, users must access the appliance UI from UniView (as described in To log in to the appliance UI from UniView). To disable local network access, see Disable or enable local network access to an appliance.
1. Log in to your UniView Portal:
● Open a Firefox or Chrome browser and enter https://login.backup.net/ to access the login page.
● Enter the backup.net homerealm that was provided to you by the UniView Portal Onboarding team. Click Next.
● Enter the username and password of your UniView Portal account. Click Log In.
● Enter your two-factor authentication (2FA) code, then click Verify. You can obtain the code from your authenticator app or use a recovery code.
NOTE Only use a recovery code if you have lost your IOS or Android device, or cannot access your authenticator application for some other reason.
2. In the Appliances view, click New +.
3. Do one of the following:
● Select an organization from the Name list.
OR
● Click Add New Organization and do one of the following:
● If you have integrated your PSA system ( (ConnectWise Manage, Autotask, or BMS), use the Import Organizations dialog to select an organization and scope.
● If you have not integrated a PSA system, use the Add Organization dialog to enter the organization name, select a scope, and click Save.
4. Click Next.
5. Copy the backup.net ID that displays. (Leave this dialog open. Do not click Done.)
6. Log in to the Unitrends appliance. In the Edit Appliance dialog, click Backup.net Config, then paste the ID into the Backup.net ID field. Click Save. Click OK.
7. Return to the UniView Portal. Click Done.
The appliance is added and displays in the Appliances list.
NOTES
● It can take a few minutes for the appliance to display in the list. If needed, refresh the page.
● For increased appliance security, the UniView Portal has a feature that blocks users from logging in directly to the appliance UI. Once local network access has been disabled, users must connect to the appliance from UniView. To use this feature, see Disable or enable local network access to an appliance.
UniView allows users to restrict local access to the Unitrends appliance on the local network. The appliance UI and management functions can still be accessed through UniView. Disabling local access enforces MFA, significantly reduces potential security exposure, and allows admins greater access controls through roles and scopes in UniView.
Once local network access has been disabled, users must connect to the appliance from UniView (as described in To log in to the appliance UI from UniView).
Consider the following before disabling local network access:
● To enable or disable local network access, you must log in to UniView as a Superuser, Admin, or Manage user. (UniView users with Monitor access cannot enable or disable local network access.)
● To enable or disable local network access, the Unitrends appliance must be running version 10.7.2 or higher.
● Hot backup copy to a Unitrends appliance target – To add a Unitrends appliance backup copy target to the appliance, local network access must be enabled on the backup copy target appliance. If needed, use the procedure below to enable local network access on the target appliance before adding the hot backup copy target. Once the target has been added, use the procedure below to disable local network access.
● iSeries protection – To protect your iSeries platform, you must access the appliance directly from the local network. Do NOT disable local network access if your appliance is protecting an iSeries environment.
● Appliance disaster recovery (DR) – Local network access must be enabled on the DR target appliance. Once you have recovered the configuration and last backups from the failed appliance, use this procedure to disable local network access on the target appliance.
To disable or enable local network access
1. In the Appliances view, click the appliance.
2. On the Appliance Details page, scroll down to the Settings section:
●  indicates local network access is enabled (users can access the appliance UI by entering https://<applianceIPaddress>/ui/ in a browser on the local network).
indicates local network access is enabled (users can access the appliance UI by entering https://<applianceIPaddress>/ui/ in a browser on the local network).
●  indicates local network access is disabled (users must access the appliance UI by logging in to UniView and clicking the appliance's
indicates local network access is disabled (users must access the appliance UI by logging in to UniView and clicking the appliance's  button, as described in To log in to the appliance UI from UniView).
button, as described in To log in to the appliance UI from UniView).
3. Do one of the following:
● Click  to disable local network access.
to disable local network access.
● Click  to enable local network access.
to enable local network access.
NOTES
● If the toggle is disabled ( ), you are using Monitor user credentials and cannot enable or disable local network access.
), you are using Monitor user credentials and cannot enable or disable local network access.
● It may take a minute or two to disable or enable access. During this transition time, the  or
or  toggle is disabled (
toggle is disabled ( ).
).
● If the appliance is not running version 10.7.2 or higher, this feature is not supported and you see this message: 
IMPORTANT If this appliance is managed by UniView (e.g., users can only log in to the appliance UI from UniView), local network access to the appliance is disabled. Before removing the appliance from the UniView Portal, you must enable local network access if users will still need access the appliance UI. For details, see Disable or enable local network access to an appliance.
1. Log in to your UniView Portal:
● Open a Firefox or Chrome browser and enter https://login.backup.net/ to access the login page.
● Enter the backup.net homerealm that was provided to you by the UniView Portal Onboarding team. Click Next.
● Enter the username and password of your UniView Portal account. Click Log In.
● Enter your two-factor authentication (2FA) code, then click Verify. You can obtain the code from your authenticator app or use a recovery code.
NOTE Only use a recovery code if you have lost your IOS or Android device, or cannot access your authenticator application for some other reason.
2. In the Appliances view, click the appliance.
3. On the Appliance Detail page, click ![]() . Type DELETE and click the Delete button.
. Type DELETE and click the Delete button.
4. Log in to the Unitrends appliance. In the Edit Appliance dialog, click Backup.net Config, then click Remove. Click OK.
The VM replicas feature creates standby replicas of critical VMs that can be brought online in seconds. During replica setup, the user specifies the number of recovery point snapshots to retain with the replica VM on the hypervisor.
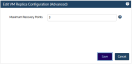
By default, the appliance supports retention of up to 14 replica snapshots. You can modify the maximum number allowed by the Unitrends appliance by doing these steps:
1. On the Configure > Appliances page, select the appliance and click Edit.
2. In the Edit Appliance dialog, click Advanced and select VM Replica Configuration.
3. Modify the number of Maximum Recovery Points. Supported values are 1-28.
4. Click Save.
You can configure your appliance to send system and application-specific alerts to your network management server using the SNMP protocol. Alerts are delivered as incoming trap messages to the network management application. This enables you to quickly identify and respond to hardware or software conditions that require action.
Through the use of the Unitrends SNMP agent and MIB, you can configure alerts to be sent to your own Remote Monitoring and Management (RMM) software.
To use the Unitrends agent:
● The appliance must be running version 9.0.0-12 or higher.
● The Unitrends SNMP agent supports SNMP gets with SNMP version 1, 2c, and 3.
1. If you will be using SNMP V3, configure the username and password from the command line as follows:
● Using a terminal emulator, such as PuTTY, connect to the appliance using the following:
● Appliance IP address
● Port 22
● SSH connection type
● Log in as user root.
● Enter the following command to configure the SNMP V3 username and password:
# /usr/bp/bin/cmc_snmpd user create<snmp_user><snmp_passwd>
The script defaults to authorization type MD5 and privacy/encryption of DES.
2. Log in to the appliance UI.
3. On the Configure > Appliances page, select the appliance and click Edit.
4. Click Advanced and select SNMP.
NOTE Your appliance comes configured with a default destination of notifications.unitrends.com. Various system alerts are sent to this address to enable Unitrends to proactively resolve problems, if and when they arise. For example, if a disk drive is failing, Unitrends receives a trap and dispatches a warranty request on the failed component (if the appliance support contract is up-to-date). This destination must remain in place for proactive monitoring to continue.
5. Click Download MIB and save the unitrends.mib.txt file.
6. Install unitrends.mib.txt in your RMM environment. The file is also available at http://<Unitrends appliance IP>/snmp/.
NOTE You will also need the Net-SNMP MIBs. These come standard in most RMM software. If you need them, they are available at http://<Unitrends appliance IP>/snmp/.
7. Return to the appliance UI. In the Trap Destinations area, click Add.
8. Enter the Destination address and Community, check Enabled, and click Save.
9. Click Test. A test trap is sent to all destinations. You see a Success message if the destination you configured is operational.
Unitrends supports Challenge Handshake Authentication Protocol (CHAP) for iSCSI connections to external storage:
NOTE CHAP authentication is used for iSCSI connections to external backup storage and backup copy targets only. CHAP is NOT used to recover files from host-level backups over iSCSI.
● You can configure the iSCSI connection with CHAP before configuring CHAP on the target storage. Once the target is configured, CHAP authentication is enforced.
● If CHAP has not been configured on the target storage, the appliance detects this and gains access without CHAP authentication, even if CHAP has been enabled on the Unitrends appliance.
● If CHAP has been configured on the storage target, you must enable CHAP authentication on the Unitrends appliance. If not, any attempt to add the target to or access the target from the Unitrends appliance fails.
● A single CHAP username and password is used by the Unitrends appliance. Therefore, all of its CHAP-enabled iSCSI targets must be configured with this username and password.
● CHAP is supported from the initiator (Unitrends appliance) to the target only. Mutual (bi-directional) CHAP is not supported.
● CHAP authentication occurs upon first log in to the target. Subsequent operations on the target succeed, without further authentication, for the duration of the iSCSI session or until the target sends a random challenge request.
1. Log in to the appliance UI.
2. On the Configure > Appliances page, select the appliance and click Edit.
3. Click Advanced and select iSCSI CHAP.
4. Verify that the Use System CHAP Credentials box is checked.
5. Enter credentials in the Username, CHAP Password, and Confirm CHAP Password fields, then click Save. One set of credentials is used to access all iSCSI targets that have been configured to use CHAP authentication.
In most cases, you use the main UI pages (Dashboard, Protect, Recover, Jobs, Reports, and Configure) for appliance administration tasks. In some cases, you may need to access additional information, such as log files, lists of running processes and services, or disk status. The Support Toolbox provides an easy way to access this lower-level appliance information and perform related tasks.
1. Log in to the appliance UI.
You must log in directly to the appliance. You cannot access the Support Toolbox of a managed appliance.
2. On the Configure > Appliances page, select the appliance and click Edit.
3. Click Advanced and select Support Toolbox.
4. The Support Toolbox (Advanced) dialog displays.
● Scroll through the toolbox to find the information or task you are interested in.
● Hover over the options to see descriptions and helpful tips.
● Click an item to run a command. Click Close to exit.
5. Click Close to exit.
The appliance is automatically configured to use the best settings for the appliance model and other factors in your environment. In most cases you will never need to modify these settings. If you are an advanced user and want to adjust deep configuration settings, such as MaxBlockSize and QuickSeek, you can edit these settings. Do not modify these settings if you are not familiar with how the change will impact appliance performance and on-appliance retention.
1. Log in to the appliance UI.
You must log in directly to the appliance. You cannot change the configuration settings of a managed appliance.
2. On the Configure > Appliances page, select the appliance and click Edit.
3. Click Advanced and select General Configuration.
4. Scroll or use the column sort and filter fields to view appliance settings.
● Click on any column to sort alphabetically (a to z). To reverse the order (z to a), click again.
● Filter the display by entering text in a column's filter field.
5. (Optional) Modify a setting. Select the setting, enter a new Value, then Save. Repeat this step as needed to modify additional settings.
6. Click Close to exit.
NOTE This feature applies to Unitrends Backup appliances only.
When deployed, the Unitrends Backup database is located in the same partition as stored backups. You now have the option to configure a separate partition to house the Unitrends Backup database. With this configuration, the database resides in its own partition on a separate logical volume than the backups themselves. Use this option to increase backup performance and stability by using faster performing storage for the database and lower-tier storage for the backup data itself. This is great when you are using slower backup storage that communicates with Unitrends Backup over NFS or CIFS protocols.
By moving the database to a different location than the stored backups, you add hardware. This introduces additional potential points of failure. Be sure to:
● Implement proper measures to ensure hardware reliability of all storage.
● Store copies of your backups on secondary storage to avoid losing backup data in the event of a hardware failure. For details, see Backup copies.
These requirements must be met to create a separate database partition:
● The appliance must be a Unitrends Backup appliances.
● To create a separate database partition, you must first add a disk to the Unitrends Backup appliance.
● The disk you add must be at least 100GB or twice the running database size, whichever is greater.
● To create the database disk, Unitrends recommends that you add a disk in the same way you added the initial backup storage during Unitrends Backup deployment. For example, if you created the initial backup storage using direct attached storage (DAS), use DAS for the database partition. For details, see the applicable Unitrends Backup deployment guide:
● Deployment Guide for Unitrends Backup on VMware
● Deployment Guide for Unitrends Backup on Hyper-V
● Deployment Guide for Unitrends Backup on Citrix XenServer
● Deployment Guide for Unitrends Backup on Nutanix AHV
● Deployment Guide for Unitrends Backup in Azure
● Deployment Guide for Unitrends Backup in Amazon Web Services
● Deployment Guide for Unitrends Free on VMware
● Deployment Guide for Unitrends Free on Hyper-V
WARNING! Unitrends strongly recommends that all Unitrends Backup storage is either direct attached storage (DAS, internal to the hypervisor) or resides on one external storage array. If you configure storage across multiple storage arrays and one becomes unavailable, all backup data ends up corrupted, resulting in total data loss.
Once the above requirements have been met and you have added the database disk to your Unitrends Backup appliance, proceed to To create a separate database partition on your Unitrends Backup appliance to set up the partition and migrate the database.
This procedure assumes you have added a disk to your Unitrends Backup appliance that meets the requirements above.
1. Using a terminal emulator, such as PuTTY, connect to the appliance using the following:
● Appliance IP address
● Port 22
● SSH connection type
2. Log in as user root.
3. Issue this command to download the create database partition script:
# wget https://sftp.kaseya.com/utilities/newdisk
4. Issue this command to add execute permissions:
# chmod +x newdisk
5. Issue this command to run the script:
# ./newdisk
6. In the script output, you see one of the following:
● Output similar to the following, indicating that an eligible database disk is available. Note the device partition (/dev/sdd in the example). You will need it in the next step. Proceed to step 7.
Available added disk = /dev/sdd (size 107.2 GB)
● The following message, indicating that an eligible disk is not available. Add an eligible disk and rerun this procedure.
No available added disks found
● A message similar to the following, indicating that the disk you added is less than 100GB in size. Add an eligible disk and rerun this procedure.
Disk /dev/sdd size X GB is less than minimum 100 GB
● A message similar to the following, indicating that the disk you added is less than twice the current database size. Add an eligible disk and rerun this procedure.
Disk /dev/sdd size X GB is less than twice database X GB
7. Issue the cmc_stateless dbpart command followed by the device partition you noted above to format the disk and migrate the database. The following example uses /dev/sdd as the device partition:
# cmc_stateless dbpart /dev/sdd
NOTES
● This feature applies to Unitrends Backup virtual appliances only.
● For Unitrends Backup on Citrix XenServer, the appliance is configured to optimize retention (Level 3) because only full backups are supported.
● Level 3 is required for ransomware detection functionality.
Deduplication is a data compression technique that eliminates duplicate data blocks. To yield fastest performance, the Unitrends Backup appliance is configured to use the Level 1 deduplication setting. You can opt to modify this setting to increase on-appliance retention. Keep in mind that increasing the deduplication level decreases job speed.
To configure deduplication settings:
1. Log in to the appliance UI.
2. Click the gear icon and select Deduplication Settings.
3. Select one of the following deduplication settings:
● Level 1 — Use this setting to optimize performance.
● Level 2 — Use this setting to balance performance and on-appliance retention.
● Level 3 — Use this setting to optimize retention.
4. Click Apply Settings.
The Unitrends agent needs access to the appliance's Samba share for backup and recovery operations. The SMB 2.0 security option is enabled by default on Unitrends appliances that were originally imaged or deployed with version 10.4.8 or higher. (The SMB 1.0 security option is enabled by default on appliances that were originally imaged or deployed with a pre-10.4.8 version. Upgrading the appliance does not change the SMB 1.0 setting.)
The following requirements apply to appliances configured with SMB 2.0:
NOTE See How Unitrends supports SMB2 for SMB 2.0 configuration procedures.
|
Feature |
SMB 2.0 Requirements |
|---|---|
|
Oracle on Solaris |
The Unitrends agent must have access to the appliance's SMB 2.0 Samba share to perform backup and recovery operations. These requirements apply: ● A Samba client must be enabled. See How Unitrends supports SMB2 for details. ● A Samba key must be added for the backup appliance. To add the key, issue this command (the default password is samba): smbadm add-key -u samba@<applianceIP> |
|
Oracle on Windows |
SMB 2.0 must be enabled on the Windows server so that the Unitrends agent can access the appliance's SMB 2.0 Samba share when performing backup and recovery operations. |
|
Recover files from host-level backups of Windows VMs |
To use a CIFS share for the recovery, SMB 2.0 must be enabled on the target Windows asset. |
|
SharePoint |
To perform backup and recovery operations, SMB 2.0 must be enabled on each node in the farm. NOTES ● SharePoint 2007 on Windows 2003 and prior is not supported on SMB 2.0 appliances. (To configure your appliance to use SMB 1.0, see How Unitrends supports SMB2.) ● SharePoint may require custom client configuration for use with SMB 2.0. If SharePoint backups do not run successfully, see this Microsoft article for client configuration details: SharePoint Ports, Proxies and Protocols...An overview of farm communications. |
|
Windows agent push |
To push install the Windows agent, SMB 2.0 must be enabled on the Windows asset. |
|
Windows replica on Hyper-V |
To run a Windows replica on Hyper-V, SMB 2.0 must be enabled on the Hyper-V server. |